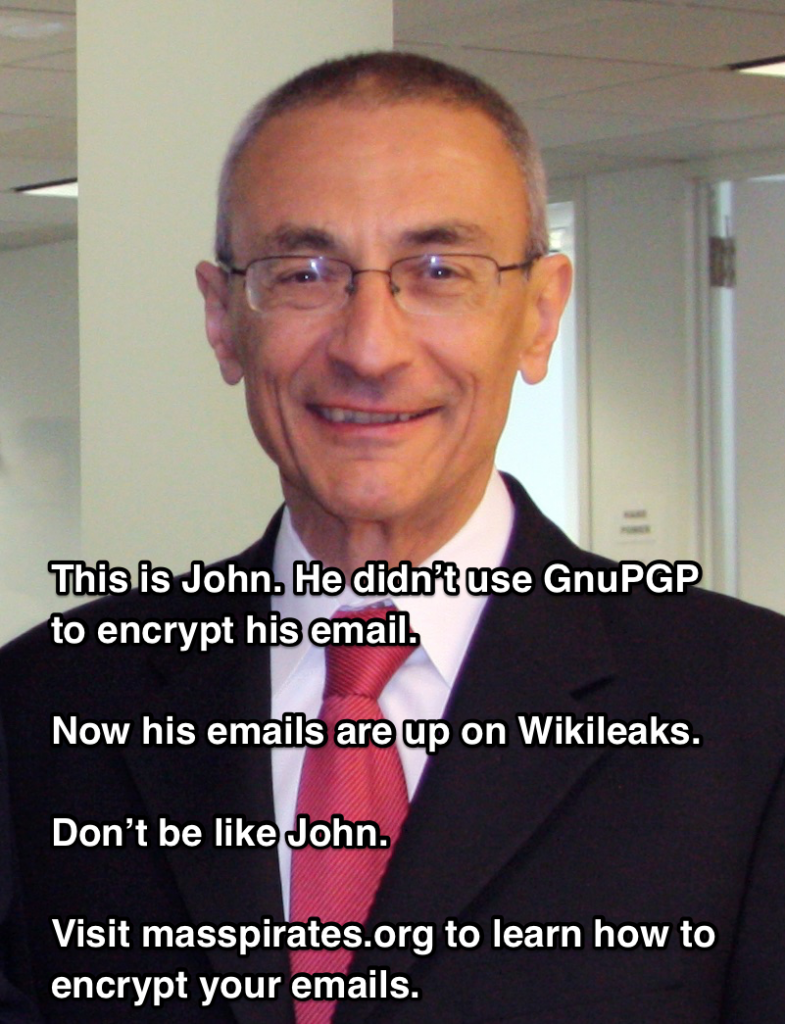
 This is John.
This is John.
He didn’t encrypt the text of his email using GnuPGP.
He didn’t insist that all of the email sent to him be encrypted.
He didn’t use secure communications free from malicious hackers, the NSA or friends of the NSA, such as Yahoo.
Now his emails are up on Wikileaks.
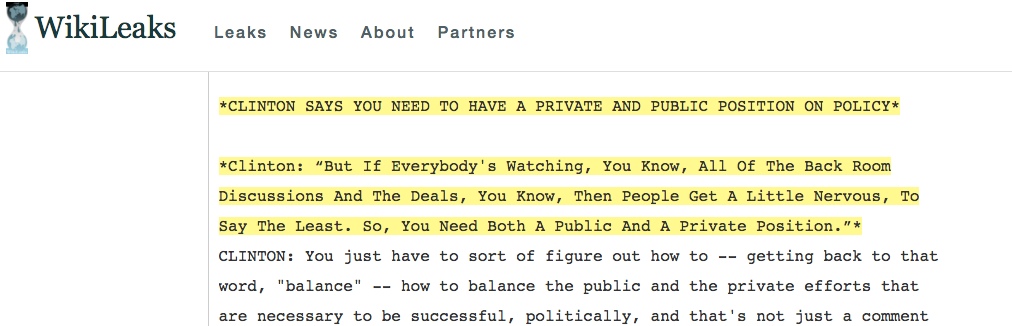
John is embarrassed and his friend Hillary has to answer lots of questions.
Don’t be like John.
Learn to encrypt your emails.
Everyone needs to know their private communications are actually private. Private from abusive ex-lovers, phishers, malicious hackers or the NSA.
There are many ways you can learn to protect your email and your privacy on-line:
Protect yourself. Be sure you aren’t the next John.
Image of John Podesta from Wikipedia licensed under the Creative CommonsAttribution 2.0 Generic license.
Image of email from Wikileaks.

He didn’t encrypt the text of his email using GnuPGP.
He didn’t insist that all of the email sent to him be encrypted.
He didn’t use secure communications free from malicious hackers, the NSA or friends of the NSA, such as Yahoo.
Now his emails are up on Wikileaks.
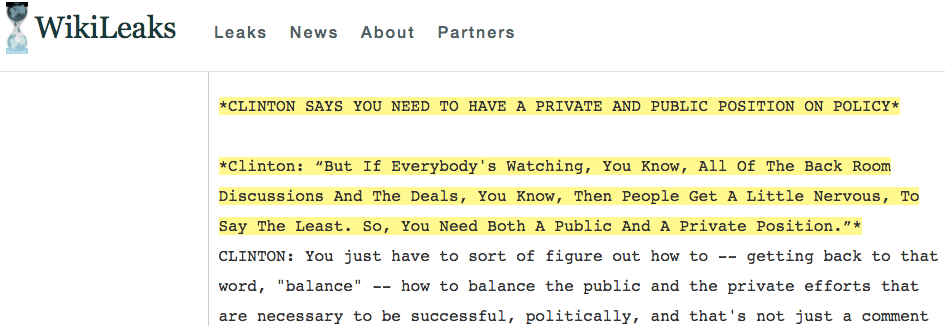
John is embarrassed and his friend Hillary has to answer lots of questions.
Don’t be like John.
Learn to encrypt your emails.
Everyone needs to know their private communications are actually private. Private from abusive ex-lovers, phishers, malicious hackers or the NSA.
There are many ways you can learn to protect your email and your privacy on-line:
Protect yourself. Be sure you aren’t the next John.
Image of John Podesta from Wikipedia licensed under the Creative CommonsAttribution 2.0 Generic license.
Image of email from Wikileaks.